 By B.N. Frank
By B.N. Frank
Utility “Smart” Meters (electric, gas, and water) have been plagued with problems – including serious security vulnerabilities – since they started being deployed.
Last August, IBM warned about a security flaw in millions of Internet of Things (IoT) devices including “Smart” Meters and medical implants. More scary reports about millions of IoT devices – including “Smart” Meters – was also reported in December.
FCW recently reported about warnings from the Cybersecurity and Infrastructure Security Agency (CISA):
IoT cyber law signed amid growing vulnerabilities
On December 4th, President Trump signed the IoT Cybersecurity Improvement Act of 2020, which directs the National Institute of Standards and Technology (NIST) to create standards and guidelines on the use and management of internet of things devices by federal agencies and to develop guidance on vulnerability disclosure and the resolution of disclosed vulnerabilities.
The bill could not be any more timely. Four days after the act was signed into law, the Cybersecurity and Infrastructure Security Agency (CISA) released an advisory on AMNESIA:33, a set of 33 vulnerabilities impacting four open source TCP/IP stacks which collectively serve as the foundational components of millions of connected devices worldwide. Forescout Research Labs reported these vulnerabilities.
AMNESIA:33 impacts both IoT (e.g., smart plugs, cameras, sensors, smart lights, etc.) and operational technology devices (e.g., physical access control, fire and smoke alarms, energy meters, etc.) from more than 150 vendors. These vulnerabilities can be exploited to take full control of a target device, impair its functionality, obtain potentially sensitive information or inject malicious DNS records to point a device to an attacker-controlled domain.
Vendors affected by AMNESIA:33 might have benefited from existing NIST IoT guidance. This guidance, including NISTIR 8259: Recommendations for IoT Device Manufacturers: Foundational Activities and NISTIR 8259A Core Device Cybersecurity Capability Baseline, focuses primarily on pre-market activities by the device manufacturer. Both publications seek to educate device manufacturers everywhere on making equipment that can be used safely, with improved configuration and other features for more effective management.
But what happens after the devices are purchased and deployed?
The passage of the IoT Cybersecurity Improvement Act of 2020 means that NIST will start to address the gap in post-market guidance to help organizations adequately address newly discovered vulnerabilities in devices already on their networks.
While the bill only specifies four IoT-related topics that NIST must address (secure development, identity management, patching and configuration management), forthcoming guidance should include much more if the goal is to secure organizations from potentially insecure IoT devices.
For example, many vendors are still assessing whether they are affected by AMNESIA:33 and may not release patches immediately; some may not release patches at all. Further, because of the embedded nature of the AMNESIA:33 vulnerabilities, a traditional vulnerability scan across the network will not detect them. In developing guidance, NIST has to be mindful of situations where traditional methods are lacking and offer alternative approaches to secure organizations.
NIST’s forthcoming IoT guidance should include instructions on how to apply NIST cybersecurity framework core functions (identify, protect, detect, respond and recover) in environments where IoT devices are increasingly prevalent. It should also include cybersecurity best practices beyond those specified in the bill’s text, like network segmentation, and highlight the importance of basic cybersecurity activities, such as asset inventory, that provide a baseline or “one source of truth” for accurate remediation. Asset inventory, for example, is critical when addressing embedded software; organizations need to know what devices are affected then find them on their networks, which is easier said than done, especially if good detection tools are lacking.
While the discovery of any vulnerability that affects millions of connected devices can be shocking, the IoT Cybersecurity Improvement Act signals how the attention of policymakers is appropriately focused on the cybersecurity threat posed by IoT devices. The AMNESIA:33 disclosure shows they have good reason to be concerned. As NIST builds on existing IoT work to develop new guidance, timely disclosures remind experts that securing IoT is about tracking and securing components, and scaling detection and response will be paramount.
I urge NIST in forthcoming guidance to more fully address the myriad challenges in securing IoT devices, especially since traditional methods like scanning or patching may be inadequate to combat real vulnerabilities.
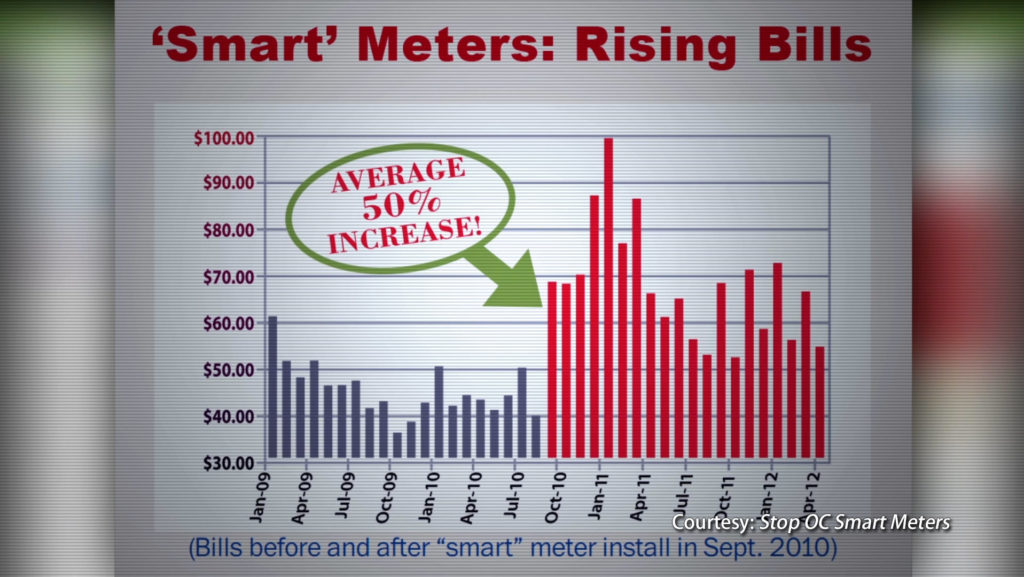
Utility “Smart” Meters were never necessary. They have never saved meaningful amounts of energy and customer rates are usually increased for their installation AND frequent replacement (see 1, 2, 3, 4). They are extremely profitable to utility companies though because they are 2-way transmitting whereas original analog meters are not. This feature allows utility companies to remotely turn off services and ration customer usage. It also allows them to collect minute-by-minute usage data which they can analyze in order to market more products and services to customers. Utilities can also sell this data to 3rd parties (see 1, 2).
Since tens of millions of “Smart” Meters have been deployed, it is likely they have been installed on your home and throughout your community. More installations are planned despite all the problems associated with them – fires, explosions, higher bills, malfunctioning and broken appliances, cybersecurity risks (see 1, 2), and health issues in people and animals (see 1, 2, 3, 4, 5, 6, 7, 8, 9).
There has been so much opposition to these meters that some utility companies started allowing customers to “opt out” of them. Online documentary – Take Back Your Power – provides more details about these horrible devices.
Activist Post reports regularly about “Smart” Meters, IoT, and other unsafe technology. For more information, visit our archives and the following websites:
- Coalition to Stop Smart Meters
- EMF Safety Network
- Stop Smart Meters
- SmartMeterHarm
- Smart Grid Awareness
- Smart Meter News
- Take Back Your Power
- The People’s Initiative
- Wireless Information Network
Subscribe to Activist Post for truth, peace, and freedom news. Send resources to the front lines of peace and freedom HERE! Follow us on SoMee, HIVE, Parler, Flote, Minds, MeWe, Twitter and Gab.
Provide, Protect and Profit from what’s coming! Get a free issue of Counter Markets today.

Be the first to comment on "CISA Warns about Cyber Vulnerabilities with Utility “Smart” Meters and Other IoT Devices"